Nine of Hearts
The 9_of_hearts.png flag was a frustratingly simple flag, but forced the player to learn about the esoteric operating system.
Topics covered:
- CVE-2006-2369
- X11 Forwarding
- Plan 9 OS Fossil file system
Apologies in advance for the lack of images, I originally did not intend to do a writeup so I did not document the process very well.
Funny side note, Metasploit supports Plan 9 OS.
Remote Enumeration
Scanning the target host with nmap reveals port 5900 is open, commonly used for VNC, built on top of the Remote Frame Buffer Protocol.
Using the -A option to run NSE scripts with nmap reveal the version of VNC to be RealVNC 4.1.0. Since this is the Metasploit CTF, we can be certain there is probably something in metasploit to leverage this vulnerability.
Sure enough, auxiliary/admin/vnc/realvnc_41_bypass exists for this exact purpose, found using the search functionality in msfconsole.
Additionally, ExploitDB gives us CVE-2006-2369 a python alternative PoC, the only difference being this one runs vncviewer for you.
Exploitation
Since vncviewer requires X11 for the session window, we will need to use ssh for X11 forwarding. I will not cover all the details on ensuring your settings are correct, but a comprehensive guide can be found here. We use SSH to connect to the jump box.
ssh -i msfctf.pem -X -C ec2-user@<jumpbox>Note the -C, which uses the gzip compression algorithm to compress data across the wire. This was used only because my ping was quite high during the CTF, and therefore the compression helped reduce the single-packet size. Doing this over a fast connection (low ping) would likley result in a slower connection than you would otherwise have.
From the jump box, we can now run the metasploit module, and then run vncviewer after the module is running.
vncviewer 127.0.0.1::5900We could specify a whole plethora of options here, but will refrain from doing so for brevity's sake.
This will reward the player with a rio splash screen.
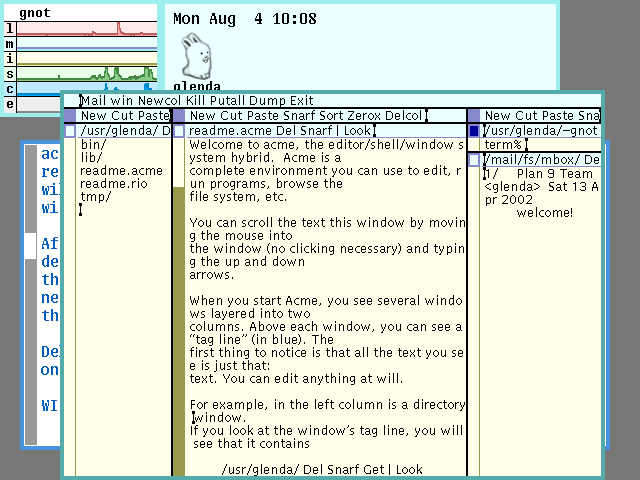
Welcome to hell.
Local Enumeration
During the enumeration phase, I found this guide extremely helpful. But first there needed to be some clean up, what a messy GUI.
After about thirty minutes of insanely frustrating attempts to control the mouse (the severe latency caused it to bounce around the screen like a rabbit on bath salts), I was able to get some resemblence of a terminal.
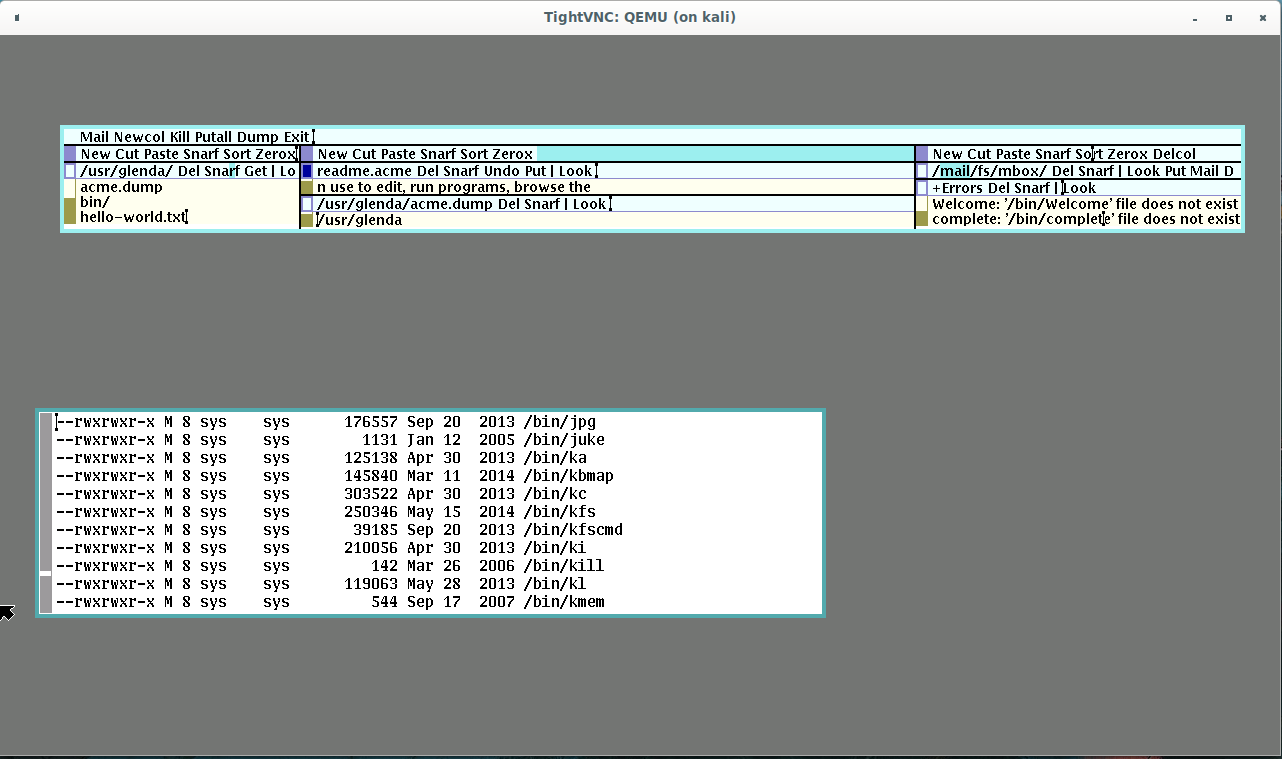
Now, a few things had been discovered while wrestling the mouse.
- The remote VNC host could be rebooted with
Ctrl+Alt+Del /bin/riowas responsible in the init process for the GUI.
So, naturally, after a little enumeration, the first command I ran was...
rm -f /bin/rioIn hindsight, I could have just moved it. But this felt oh so much better.
Anyways, this allowed us to boot into a ring 3 terminal (everything except the GUI). From here, we could start enumeration.
The first noticed detail was an interesting x.vac file, which turns out to be an archive we can uncompress with unvac. It was the /adm/ directory! Except there was no change. It was unclear whether this was a troll or a system artifact.
However, looking deeper into the .dump files and archiving features of the Plan 9 file system, it was discovered that fossil, the Plan 9 OS operating system, has a snapshot feature.
Using the Plan 9 Docs, we can see the history command allows us to see snapshots of previous files. Using this on the x.vac file doesn't prove useful, but it does show us that the snapshots exist in /n/dump/2020/.
Navigating to that directory and looking around, we eventually find a snapshot for 02JAN2020, containing 9_of_hearts.png. Thankfully, md5sum is in /bin/ so we don't have to worry about exfil.
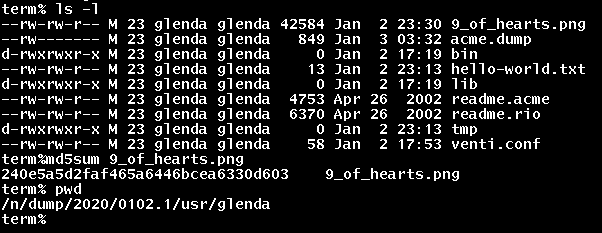
Profit!